Discovering and testing the threat vectors in your AWS environment has never been easier.
Securely integrating your Amazon Web Services (AWS) account with BreachBits can be done in 4 steps:
- Get the required BreachBits details in the Dashboard. In your BreachBits Dashboard, select 'Cloud Integrations' in the left menu.

- Once there, select 'Integrate Now' on the AWS integration tile. If you don't see the 'Integrate Now' button, then you may not have access to this feature.

- You will now be able to access the 3 pieces of information you will need to create your AWS integration. Keep this page up to reference these details as you enable the integration in AWS. These details are:
- Account ID: This is the BreachBits AWS Account Id needed to create an AWS role for BreachBits.
- External ID: This is a unique identifier for your organization that increases the security of the integration.
- Policy Definition: This is the definition of the policy needed by BreachBits to retrieve a list of your key AWS resources. This policy can be copied using the clipboard button in the upper right corner of the AWS Policy Definition Viewer.

- Once there, select 'Integrate Now' on the AWS integration tile. If you don't see the 'Integrate Now' button, then you may not have access to this feature.
- Create an AWS Policy for BreachBits. Log into your AWS account and navigate to the AWS IAM page. In the Access Management menu, select 'Policies'.

- On the Policies page, select 'Create Policy' at the top of the page.

- In the Policy Editor, select the 'JSON' tab.
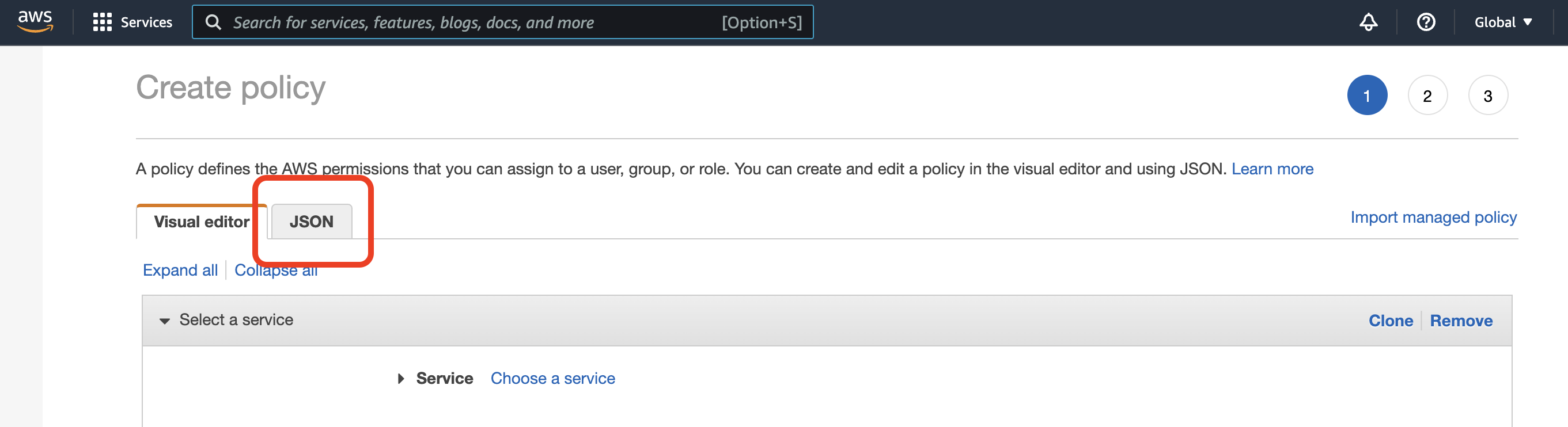
- In the 'JSON' tab, delete all text in the editor (typically Version and an empty Statement list). Then, take the text copied from the BreachBits Policy Definition in step 1 and paste it into the editor. When complete, select 'Next'.
- (optional) On the next page, you can add any tags to your policy if you wish. Once complete, select 'Next' again.
- To complete your AWS Policy for BreachBits, give it a name you will recognize and select 'Complete Policy' at the bottom of the page.
- On the Policies page, select 'Create Policy' at the top of the page.
- Create an AWS Role for BreachBits. In the AWS IAM menu, select 'Roles'.

- In the Roles page, select 'Create Role'.
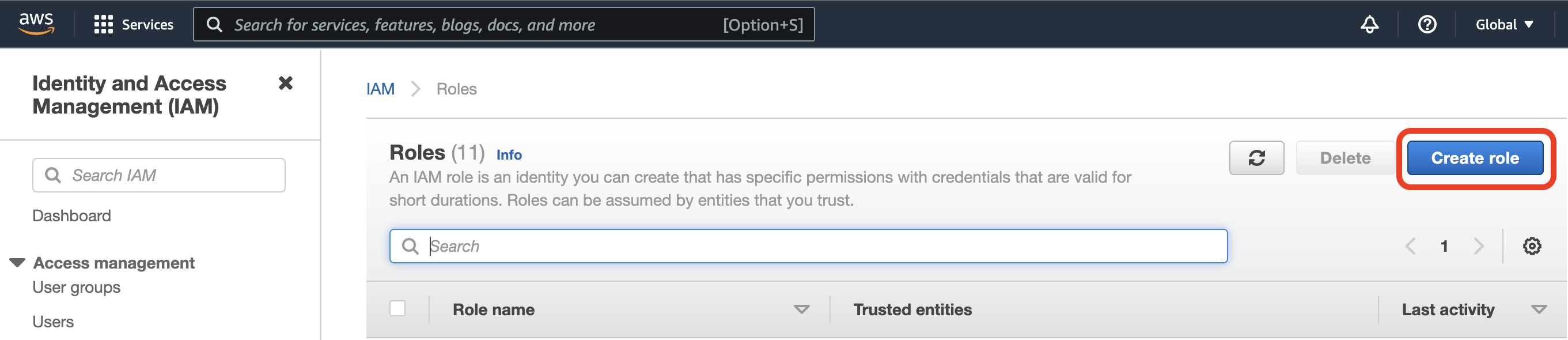
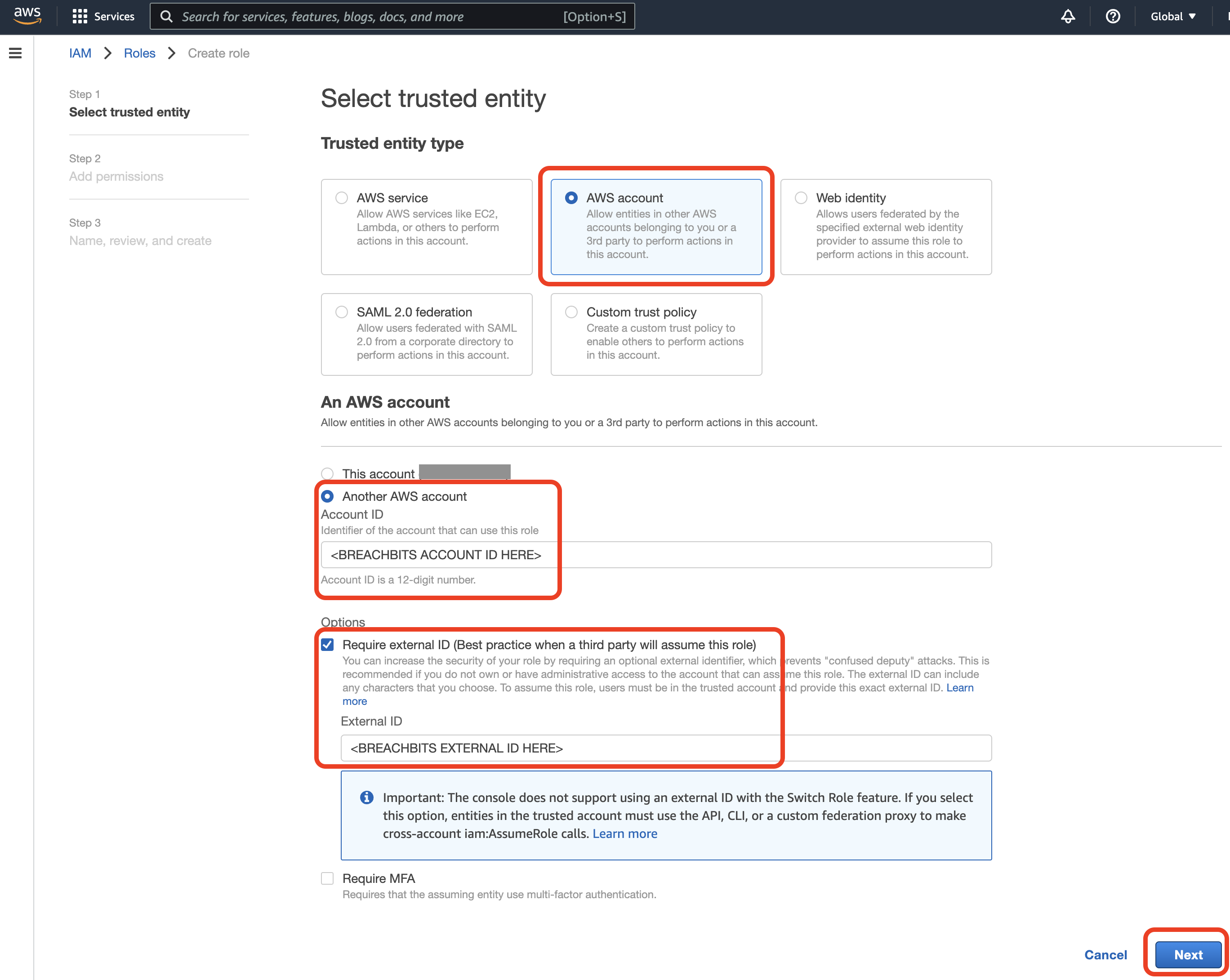
- Create the role for BreachBits using the details found in the first step.
- Trusted entity type: AWS Account
- AWS Account: Another AWS Account (provide Account ID)
- Options: Require external ID (provide External ID)
- Select 'Next'
- On the 'Add Permissions' page, select the Policy created in Step 2. Select 'Next'
- On the 'Review' page, give the role a name (required), description (optional) and any tags desired (optional). Then select 'Create Role'.
- Lastly, return to the 'Roles' page from the IAM menu and select the role that was just created.
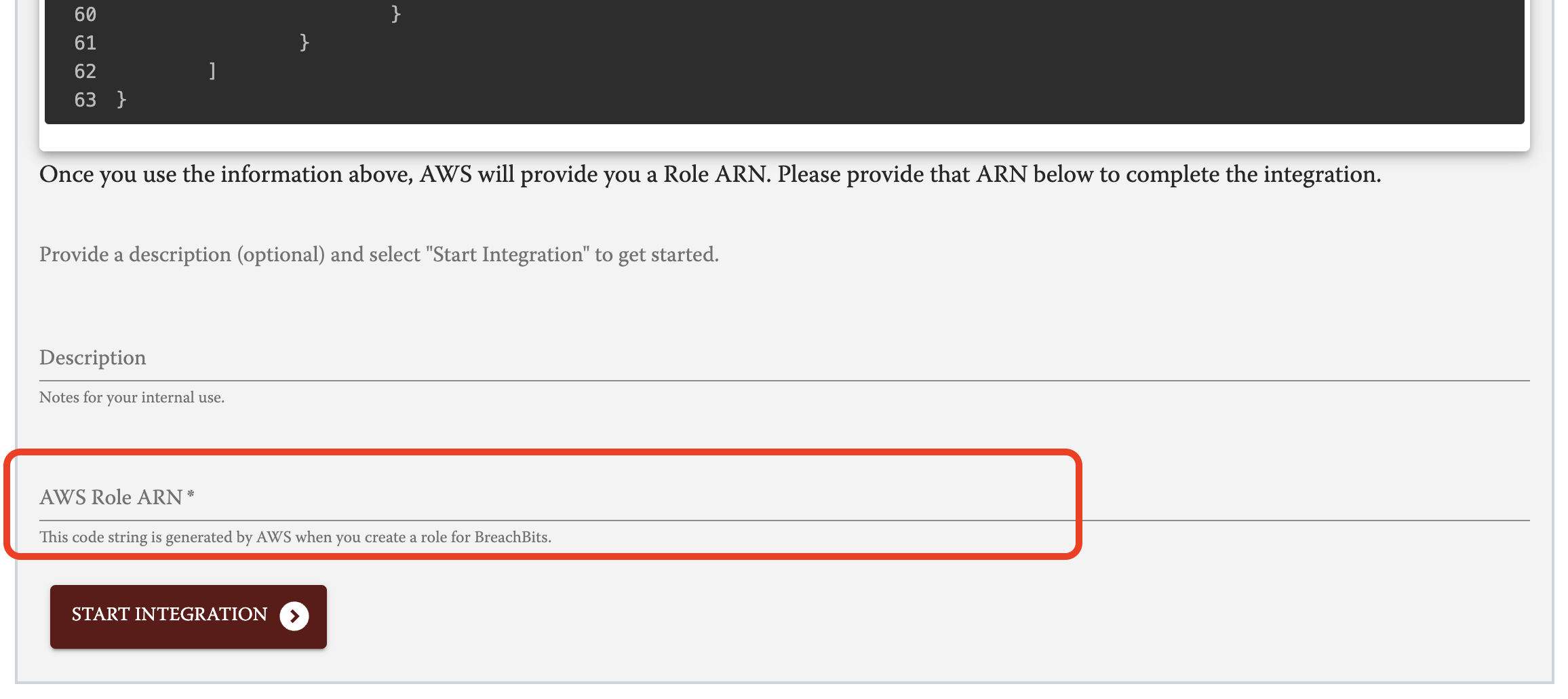
- Find the Amazon Resource Name (ARN) for the newly-created role and copy it. This is the last piece of information needed to complete the integration.

- In the Roles page, select 'Create Role'.
- Complete the integration with the AWS ARN. Return to the AWS integration page in your BreachBits Dashboard. Scroll to the bottom to find the form to enter the AWS ARN. Once you have entered it, select 'Start Integration'.
Congratulations! You have integrated your AWS infrastructure with BreachBits. The AWS Integration tile should indicate that your integration is active.
What happens next?
Now that your AWS infrastructure is integrated with BreachBits, each upcoming BreachRisk™ assessment will query your AWS infrastructure details from the integration and include it in your attack surface, where it will be searched for publicly-accessible threat vectors that can be discovered, monitored and tested.
